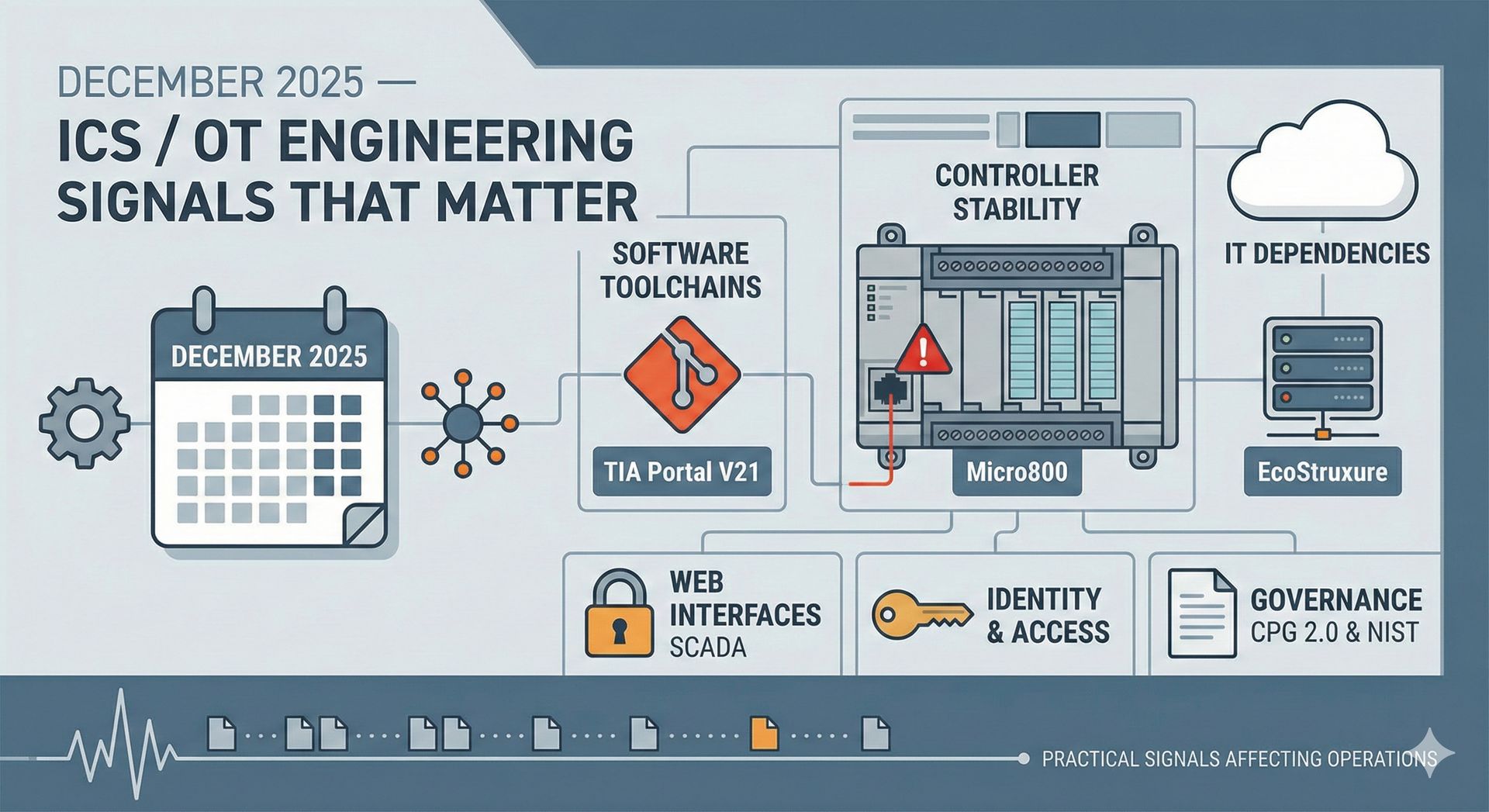
December did not introduce new threat classes or architectural ideas. What it did provide was a dense set of practical signals around software lifecycle, controller robustness, and dependency risk. These signals affect how systems are upgraded, patched, and operated, rather than how they are designed from first principles.
This issue focuses on changes that materially affect engineering work and operational decisions.
Engineering Toolchains Are Becoming Software Toolchains
Siemens TIA Portal V21
Siemens released TIA Portal V21 in late 2025, with active promotion through December. The most significant change is the introduction of source-based project exports that allow PLC logic, data blocks, and data types to be handled in standard version control systems such as Git. This applies across LAD, FBD, and SCL.
From an engineering standpoint, this enables traceability and collaborative workflows that were previously difficult or impossible with binary project formats. It does not change how controllers execute logic, but it changes how changes are reviewed, audited, and rolled back.
Siemens also updated firmware for S7-1500 and S7-1200 G2 controllers. One documented improvement is support for certain structural data block changes without forced re-initialization. Historically, these changes required stopping the controller and resetting values, increasing commissioning and maintenance risk. The new behavior reduces disruption in defined scenarios but still requires validation and testing.
New hardware announced alongside V21 supports higher-performance motion control through multicore processing. This is relevant primarily for applications with high motion object density or tight cycle constraints.
Siemens press release: https://press.siemens.com/global/en/pressrelease/tia-portal-v21-combines-engineering-efficiency-higher-plant-availability
Independent overview: https://www.parmley-graham.co.uk/content/2025/12/tia-portal-v21/
Technical release notes: https://www.cncdesign.co.nz/blog/new-tia-portal-v21-be-released-4th-december
Controller Stability and Network Stack Fragility
Rockwell Automation Micro800
On December 18, CISA published an advisory affecting Rockwell Micro820, Micro850, and Micro870 controllers. The advisory documents vulnerabilities where malformed IPv6 or CIP traffic can place controllers into fault states. In some cases, recovery requires a power cycle before faults can be cleared.
These issues originate in network stack handling rather than user logic. Systems with IPv6 enabled but unused are specifically exposed. CISA lists disabling unnecessary protocol functionality as a mitigation.
Separately, engineers have reported firmware update failures and recovery issues on Micro800 platforms in public forums. These reports are anecdotal and not part of the official advisory, but they highlight an operational concern: firmware updates themselves may carry non-negligible risk in some environments. This complicates patch planning where hardware redundancy or recovery options are limited.
CISA advisory ICSA-25-352-07: https://www.cisa.gov/news-events/ics-advisories/icsa-25-352-07
Rockwell advisory SD1766: https://www.rockwellautomation.com/trust-center/security-advisories/advisory.SD1766.html
Community discussion (non-authoritative): https://www.reddit.com/r/PLC/
OT Software Exposed Through IT Dependencies
Schneider Electric EcoStruxure
Schneider Electric advisories published in December highlight risks introduced through underlying IT services. The EcoStruxure Foxboro DCS Advisor, an optional monitoring and diagnostics service, was identified as being affected by a critical vulnerability in Microsoft Windows Server Update Services.
Successful exploitation could allow remote code execution on the server hosting the advisor component. Mitigation requires applying Microsoft patches, which may involve system restarts. This raises practical questions about where such advisor services should be hosted and how tightly they should be coupled to control environments.
A separate advisory addressed vulnerabilities in older versions of EcoStruxure Power Monitoring Expert. While supported versions can be patched, earlier releases require full upgrades due to end-of-life status. This reflects a recurring challenge in long-lived industrial systems where security upgrades are driven by software lifecycle rather than functional need.
Foxboro DCS Advisor advisory: https://www.cisa.gov/news-events/ics-advisories/icsa-25-352-02
PME advisory context: https://www.cisa.gov/news-events/alerts/2025/12/09/cisa-releases-three-industrial-control-systems-advisories
SCADA Web Interfaces as Escalation Points
Advantech WebAccess and ScadaBR
CISA published an advisory in December covering multiple vulnerabilities in Advantech WebAccess/SCADA, including unrestricted file upload and SQL injection. These vulnerabilities allow authenticated users with low privileges to escalate access and potentially execute code on the SCADA server.
Updated versions are available, but patching may require downtime or architectural changes that not all deployments can accommodate.
In early December, CISA also added a ScadaBR cross-site scripting vulnerability to the Known Exploited Vulnerabilities catalog. The CVE itself is several years old, but its inclusion indicates active exploitation. ScadaBR remains in use in some municipal and small-scale systems, often with limited monitoring. The vulnerability affects the web interface and can be used to manipulate operator views and logs.
Advantech WebAccess advisory: https://www.cisa.gov/news-events/ics-advisories/icsa-25-352-06
ScadaBR KEV notice: https://linuxsecurity.com/news/security-vulnerabilities/scadabr-xss-bug
Identity and Physical Access Issues in Engineering Systems
Siemens IAM and Energy Devices
Two Siemens advisories from December addressed non-process risks. One involved improper certificate validation in Siemens IAM clients used by engineering tools such as NX and Solid Edge. Under certain conditions, this allows man-in-the-middle attacks during authentication.
Another advisory affected Siemens Energy devices, where a documented USB reset mechanism allowed administrative access if physical access was available. Updated firmware removes this functionality. These issues are not related to controller logic but affect trust and access control in engineering and energy environments.
Siemens IAM advisory: https://www.cisa.gov/news-events/ics-advisories/icsa-25-345-04
Siemens Energy advisory: https://www.cisa.gov/news-events/ics-advisories/icsa-25-345-08
Governance Updates Affecting OT Expectations
CISA CPG 2.0 and NIST Manufacturing Profile
December also included updates to governance frameworks. CISA released Cybersecurity Performance Goals 2.0, aligning them more closely with NIST’s Cybersecurity Framework 2.0 and introducing a stronger emphasis on governance, third-party risk, and identity management.
NIST published an updated manufacturing profile to help map high-level cybersecurity outcomes to industrial environments. These documents do not mandate specific controls but influence regulatory expectations, supplier requirements, and audit criteria.
CISA CPG 2.0 overview: https://www.insidegovernmentcontracts.com/2025/12/cisa-releases-cybersecurity-performance-goals-2-0-for-critical-infrastructure/
NIST manufacturing profile coverage: https://industrialcyber.co/nist/nist-publishes-cybersecurity-framework-2-0-manufacturing-profile-to-help-strengthen-risk-management/
What This Means Practically
December’s developments reinforce a consistent operational reality:
Engineering environments are increasingly shaped by software lifecycle decisions.
Network stack behavior and third-party dependencies now materially affect controller reliability.
Optional services and web interfaces introduce exposure that is often underestimated.
Patch decisions must balance security improvement against recovery and downtime risk.
None of these require immediate action in isolation. Together, they affect how teams plan upgrades, segment networks, host supporting services, and assess the risk of change versus stagnation.
The same considerations will carry into 2026.